Oracle Intelligent Data Lake (IDL) Security: Role-Based Access Control & Permissions Explained
Oracle's Intelligent Data Lake (IDL) is a unified data platform built on open-source technologies like Apache Spark. It offers a centralized and secure repository for structured and unstructured data—eliminating silos, enabling powerful analytics, and empowering accurate decision-making across the enterprise. A key element of IDL’s architecture is Role-Based Access Control (RBAC), which ensures users access only what they’re authorized to—nothing more, nothing less.
5/8/20243 min read
Overview
This blog outlines how Oracle IDL implements enterprise-grade security through:
Role creation and assignment
Granular permissions across various components
Best practices for managing access in a secure, scalable way
Whether you're a security architect, data engineer, or IDL administrator, this guide helps you design and manage a secure access model in your environment.
Role-Based Security Model in Oracle IDL
RBAC in IDL allows administrators to centrally manage user access by assigning permissions to roles rather than individual users—simplifying governance and reducing complexity.
Key Capabilities
Create, Modify, and Delete Roles
Use the IDL Roles interface to define role groups such as Admins, Analysts, Developers, etc.
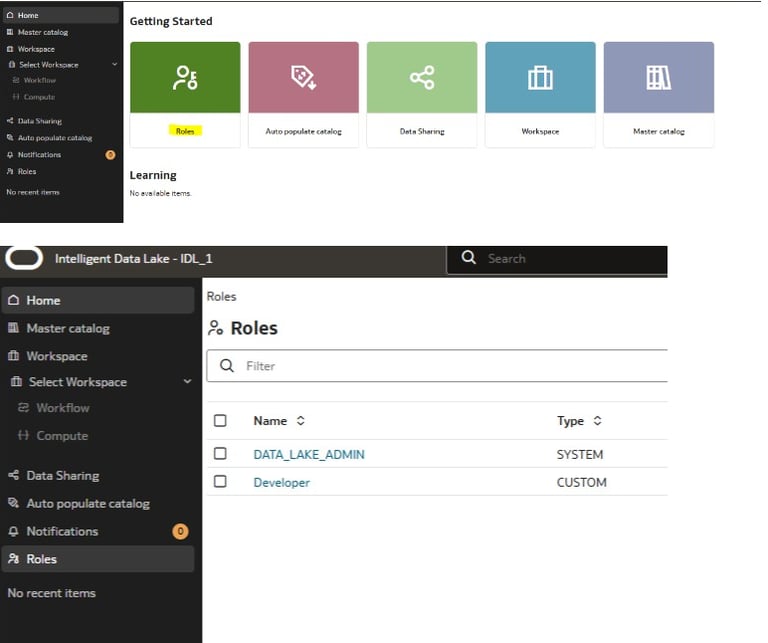
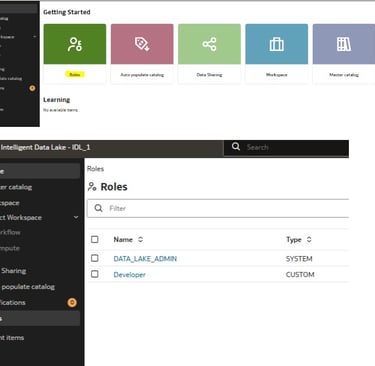
Assign Users to Roles
Select a role, navigate to the Members tab, and add users.
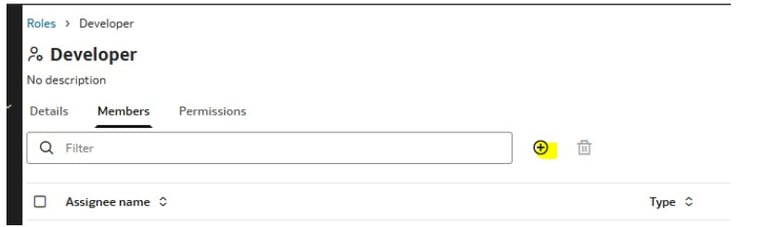

Choose the appropriate compartment and identity domain while assigning.
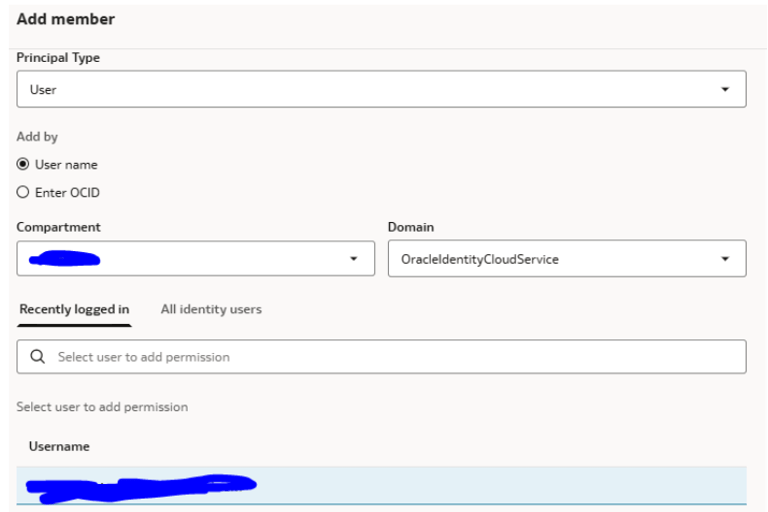
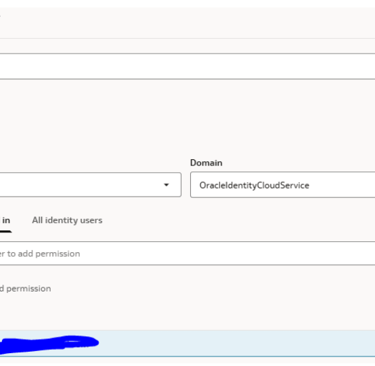
Permissions Management
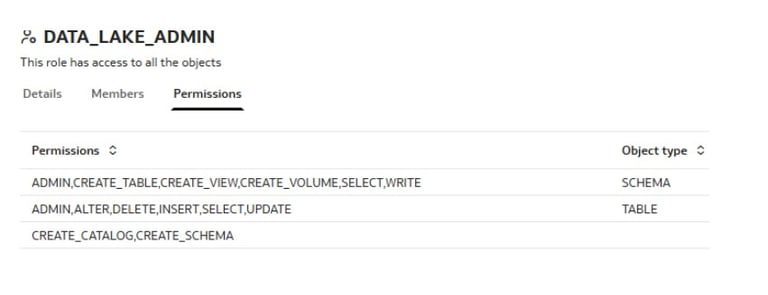
Oracle IDL provides fine-grained permissions to control user actions across all major components. Below is a breakdown of what you can control:
Oracle IDL supports permissions across critical system components, allowing tailored access based on responsibilities.e.g Admin Role will have all permissions and Developer or Specific Roles can be used to Provide permission for specific tasks.
Best Practice: Assign permissions to roles, not individual users, to simplify management at scale.
Workspace Permissions
Create, update, or delete access to workspaces where collaboration happens.
Permission to Workspace can be provided to a Role or specific user
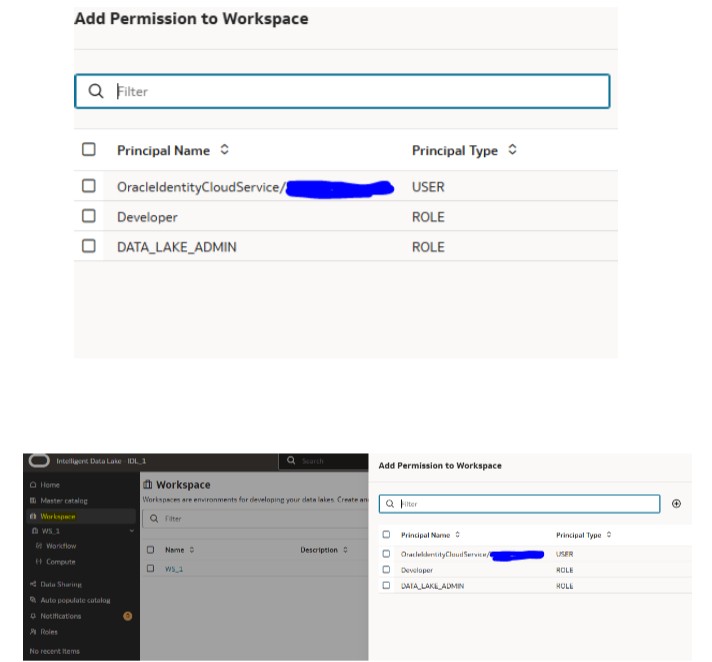
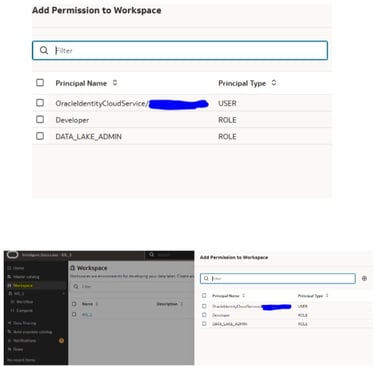
You can Create, modify, and delete file and folder permissions within workspaces to have a detailed security setup at each file level
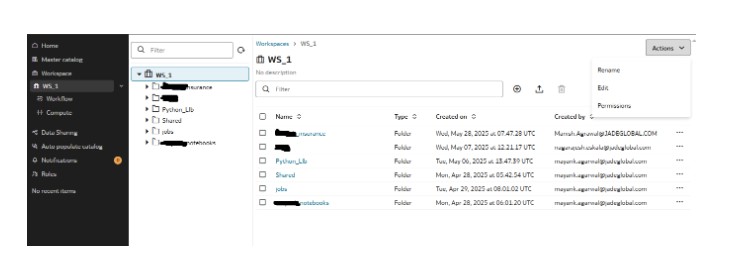
Similarly We can have separate permissions for all the below objects
File & Folder Permissions
Manage access to specific files and folders within workspaces, ideal for controlling visibility of sensitive data.
Compute Cluster Permissions
Control who can provision and manage compute resources used for data processing and analytics.
Job Permissions
Define who can submit, monitor, or terminate processing jobs.
Notebook Permissions
Manage access to notebooks used for data exploration, transformation, and visualization.
Catalog & Schema Permissions
Master and external catalog permissions: Control access to data asset registries.
Schema and table permissions: Restrict read/write/delete access to structured data entities.
Volume Permissions
Manage access to storage volumes which may house datasets or staging files.
The Importance of Secure Access Control
Security in a data lake environment isn’t just about restricting access—it's about enabling the right access to the right users at the right time. Oracle IDL's robust RBAC and permissioning model ensures:
Operational control over sensitive data
Compliance with data governance and privacy standards
Collaboration without compromising security
Implementing security in Oracle IDL isn’t just a technical necessity—it’s a strategic enabler. With structured roles and granular permissions, enterprises can unlock the full value of their data lake with trust and transparency.
Whether you're starting your IDL journey or refining your security model, setting up roles and permissions thoughtfully is a critical success factor.
Connect
Join our community for data innovation and collaboration.
Sitemap
Email : info@fdixpert.com
Phone : +91 7605848820
© 2025. All rights reserved.
